Blog
Stay updated with our new news
How do we protect a world built on math that could one day be broken?

We may soon reach a moment when the passwords and credit card numbers we rely on today are no longer enough, not because someone has hacked them, but because a new kind of computer will rewrite the rules of security entirely.
The Moment the Locks Break
Every secure connection on the internet depends on encryption that creates a “secret language” between a user and a server. When you pay a bill or send sensitive data, the information is encrypted using digital keys generated by algorithms such as RSA and ECC which are based on mathematical problems that are extremely hard for classical computers to solve.
But what happens when a new kind of machine appears? One that doesn’t play by the same rules?
Where It All Began
In 1981, physicist Richard Feynman posed a revolutionary idea:
What if we used the laws of quantum mechanics to build a computer?
And so, the concept of quantum computing was born, machines that don’t think in ones and zeros, but in every possibility at once. In classical computing, each bit is either 0 or 1. In quantum computing, each qubit can be 0 and 1 simultaneously thanks to superposition. And when qubits become entangled, they can explore millions of possibilities at once.
This isn’t just speed, it’s an entirely new way of computing.
The Quantum Threat, Simplified
In 1994, scientist Peter Shor developed an algorithm that allows quantum computers to break classical encryption. The systems behind all our digital transactions RSA, Diffie-Hellman, and ECC, can be cracked by a sufficiently powerful quantum machine in a very short time.
Since then, it has been clear that these algorithms are “secure only until the day the first large-scale quantum computer appears.” With accelerating research at Google, IBM, and Microsoft, that day is approaching faster than expected.
And because adversaries won’t wait, a new strategy emerged:
“Harvest Now, Decrypt Later.”
Attackers store encrypted data today, waiting for tomorrow’s quantum machines to decrypt it.
Reinventing the Locks: Post-Quantum Cryptography (PQC)
So how do we protect a world built on mathematics that can be broken?
The answer: we rebuild the mathematics.
This is where Post-Quantum Cryptography (PQC) comes in, a new generation of cryptographic algorithms designed to withstand quantum attacks, yet runnable on the everyday devices we use today.
Instead of relying on factoring large numbers, these algorithms use lattice-based math, hash-based systems, or error-correcting codes problems believed to be hard even for quantum computers.
The Official Turning Point
InIn 2016, the National Institute of Standards and Technology (NIST) launched a program to standardize post-quantum encryption. From 82 algorithm submissions and multiple evaluation rounds, NIST announced its first official PQC standards in August 2024:
- ML-KEM (formerly Kyber) – Key establishment
- ML-DSA (formerly Dilithium) – Digital signatures
- SLH-DSA (based on SPHINCS+) – Additional signature scheme
These algorithms are now being integrated into protocols like TLS and SSH, marking the beginning of a new era of digital security.
Lessons from Cloudflare: What Real-World Readiness Looks Like
Since 2017, Cloudflare has documented its research and early adoption of PQC to prepare for future threats.
In 2019, Cloudflare collaborated with Google to launch a large-scale internet experiment using hybrid encryption combining classical and quantum-resistant keys under the CECPQ2 project. The experiment was simple but proved that migration is possible.
When NIST announced its official PQC standards in 2024, Cloudflare immediately implemented X25519 + ML-KEM768 within TLS 1.3, and later extended PQC support to HTTP/3 via QUIC.
The result?
By September 2025, more than 40% of Cloudflare’s traffic used hybrid post-quantum encryption, and over 6 million domains were automatically upgraded to the highest security standards through its Automatic SSL/TLS system without downtime or manual configuration.
Cloudflare’s story isn’t about a hero solving the problem; it’s about a company that started early, proving that real readiness means acting today, not waiting for the crisis. But it is also a reminder that individual readiness is not enough.
Today, global server readiness for PQC is still limited and varies by protocol and platform, even as adoption accelerates across network providers and browsers.
The Countdown Has Already Begun
The internet won’t collapse overnight but it will change.
Each passing year brings us closer to the moment when quantum computers can break today’s encryption. Every message or file that isn’t protected today may be exposed tomorrow.
Mosca’s equation captures this urgency:
If X + Y > Z, you’re too late.
Where:
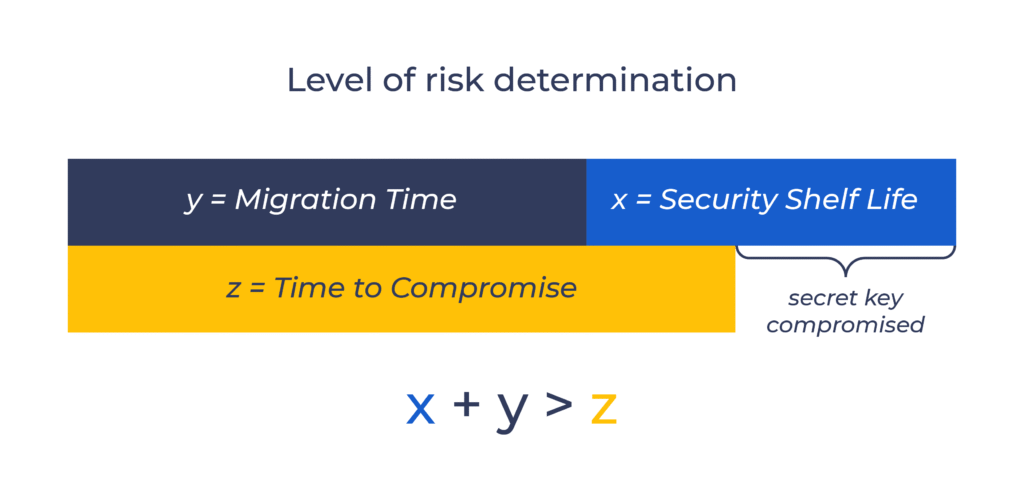
It’s not just a formula, it’s a reminder that time itself is now part of security.
We’ve already witnessed major transitions in digital security:
From HTTP to HTTPS, from passwords to two-factor authentication, from perimeter trust to Zero Trust.
The next phase is clear: from classical to quantum-resistant encryption.
From startups to governments, we will all face this transition. The real question is not whether it will happen but whether we’ll be ready when it does.
References
- Automatically Secure: how we upgraded 6,000,000 domains by default to get ready for the Quantum Future. (2025, September 24). Cloudflare.
- NIST Announces First Four Quantum-Resistant Cryptographic Algorithms. (2022, July 5). National Institute of Standards and Technology (NIST).
- The TLS Post-Quantum Experiment. (2019, October 30). Cloudflare.
Share:
More Articles

Beyond Business: ls.gives is Our Commitment to a Better Com…




Leave a Reply