Blog
Stay updated with our new news
Understanding Cybersecurity Challenges: The Evolving of Cyber Threat in 2025

Cybercrime has become the world’s third-largest economy by GDP after the U.S. and China, costing trillions of dollars annually, highlighting the critical importance of cybersecurity. What began in the 1980s with curiosity-driven viruses has evolved into a global threat affecting individuals, businesses, and governments alike.
Landmark attacks illustrate this escalation: the ILOVEYOU worm (2000) disrupted millions of email systems, Stuxnet (2010) sabotaged Iranian nuclear infrastructure, and ransomware outbreaks like WannaCry and NotPetya (2017) crippled hospitals, banks, and transportation networks worldwide.
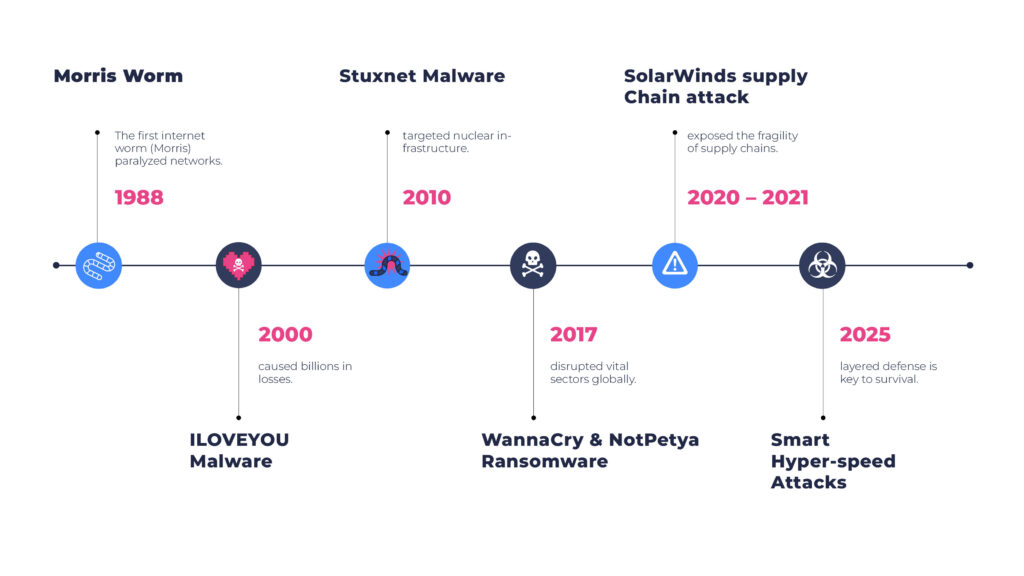
Today, cyber threats are faster, smarter, and more automated than ever, fueled by artificial intelligence and emerging risks such as quantum computing. The question is no longer if an attack will occur, but how prepared we are when it does.
The Current Face of Cybercrime
Cybercrime encompasses all forms of illegal online activity, from data theft to service disruption. Its scope has expanded dramatically:
- Malware & Ransomware: Viruses, worms, trojans, and ransomware lock files. Infostealers and double-extortion ransomware now target both data and backups. Ransomware-as-a-Service (RaaS) allows non-technical attackers to launch campaigns easily.
- Social Engineering & Phishing: Attackers trick users into revealing passwords or sensitive information. AI now generates near-perfect phishing emails and deepfake videos, making scams difficult to detect.
- Network & Service Attacks: Botnets, DDoS, and Man-in-the-Middle (MITM) attacks disrupt systems. IoT and edge devices expand the attack surface beyond traditional networks.
- Credential Attacks: Brute force and credential stuffing gain unauthorized account access. Stolen logins are sold on the dark web, fueling large-scale attacks.
- Supply-Chain & Advanced Threats: Vendors, software updates, and trusted services are prime targets. Zero-trust policies and vigilant patching defend against long-term, stealthy intrusions like Advanced Persistent Threats (APTs).
Traditional defenses like firewalls, antivirus, intrusion detection systems, encryption, Multi-Factor Authentication (MFA), VPNs, and regular patching remain essential. But in 2025, attackers exploit cloud misconfigurations, AI, deepfakes, and quantum computing risks, placing immense strain on security teams, especially those with limited resources or outdated infrastructure.
Note: Encryption scrambles data so only authorized users can access it, protecting emails, cloud files, and sensitive information. With quantum computing threatening current encryption, keeping encryption strong and up-to-date is essential
Cybersecurity Challenges in Libya
Libya’s digital growth has introduced new cyber threats. A 2024 NISSA report shows nearly 55% of system vulnerabilities remain unpatched, putting critical sectors at risk.
Over the past few years, Libyan Spider has monitored the rising cyberattacks from phishing campaigns, DDoS attacks and data leaks to hacks on critical websites, and we’ve developed and implemented effective protection solutions. At the same time, national defenses have been strengthened through key legislation, including Laws on combating cybercrime and Regulating electronic transactions.
Despite these measures, local awareness remains low, highlighting the need for education alongside technological and policy investments. While we continue to assist the community with secure infrastructure, advanced web protection, and cyber awareness programs to safeguard Libya’s digital future.
Note: In 2023, Libya ranked 90th globally in cybersecurity, scoring 28.78 on the Global Cybersecurity Index. Vulnerabilities were exposed when a May 2023 cyberattack compromised telecommunications customer data, including financial and passport information.
Building the Defense Wall
Effective cybersecurity today relies on multiple layers of defense, combining advanced technology, operational vigilance, and human awareness. At Libyan Spider, we build and enhance these defenses by implementing comprehensive solutions that protect organizations and individuals from modern cyber threats targeting email systems, cloud environments, web applications, and endpoints.
- Zero Trust Architecture forms the foundation of modern security. By never trusting users or devices by default and verifying every access request dynamically, it prevents insider threats, credential theft, and unauthorized lateral movement.
- AI and Machine Learning enhance real-time threat detection by identifying abnormal behavior and suspicious activity, enabling automated defense against phishing, ransomware, deepfake scams, and evolving attacks before damage occurs.
- Encryption and Updates protect sensitive communications, cloud files, and emails. Regular patching closes software, firmware, and operating system vulnerabilities, reducing risks from malware, ransomware, and exploitation of outdated platforms.
- Backup and Recovery strategies ensure continuity against ransomware, accidental deletions, or system failures. Secure, automated backups paired with tested recovery plans allow rapid restoration with minimal data loss.
- Endpoint Protection safeguards laptops, mobile devices, and IoT endpoints from malware, spyware, trojans, and targeted attacks, reinforcing the security perimeter in increasingly hybrid and distributed work environments.
On an individual level, cyber hygiene is key. Strong passwords, Multi-Factor Authentication (MFA), secure backups, verifying unexpected emails, and proper training prevent social engineering and identity theft. Meanwhile, AI-driven attacks, cloud vulnerabilities, and future quantum risks demand adaptive defenses and proactive risk management to meet regulations and stay ahead of evolving threats.
In 2025, cybercrime is a hyper-automated, AI-driven threat affecting everyone. For Libya, the solution lies in combining technology, policies, and awareness to build a resilient digital ecosystem.
Libyan Spider supports you with secure infrastructure, advanced protection, and awareness programs. Stay ahead of cyber threats, follow us for tips, updates, and practical guidance to safeguard yourself and your organization.
Share:
More Articles

VPS Hosting 101: How to Use Your Linux VPS to Host a Website

Stop Using Traditional VPNs: Why Cloudflare Tunnel Is the F…

Data Privacy Day: As Libya Goes Digital, Trust Becomes the…

Beyond Business: ls.gives is Our Commitment to a Better Com…

Leave a Reply